Symptom
NOTE: This article deals with computer viruses/malware. As they are constantly evolving and changing, this information is subject to change or may be out of date.
This information is provided as a guide for dealing with common scenarios we have seen, but your situation may differ. The diagnosis, removal and recovery from a malware attack is outside the scope of MIP support.
Cryptolocker is a computer virus that is usually spread through infected Email attachments. When it is activated it will go through the infected system and encrypt files it deems valuable. This will make those files inaccessible. Users usually get a warning that unless they pay a ransom their files will be deleted after a certain time.
How do I know if I have been affected by Cryptolocker?
Getting the ransom screen is a sure sign that you have been infected. But that doesn’t always happen. Within MIP the problem first manifests itself as some type of SQL connection error.

There could be a number of things not virus related that can cause this error message.
Cause
The first thing you should do is go to the machine that is the SQL server and launch the software there. If SQL Server is running and you still continue to get this message navigate to the MIP SHARE folder on your server. In that folder, access the “SQL Scripts” sub folder and scroll through the contents. Look for files that say “Decrypt Instructions”.
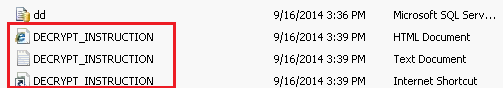
If you see the above files, then you have been infected by Cryto locker.
As of 2015 we have also seen files such as those below in the MIP Share directory:
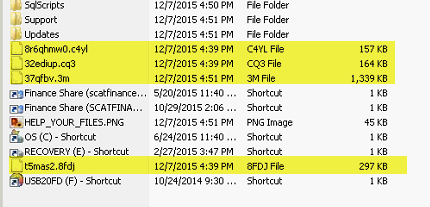
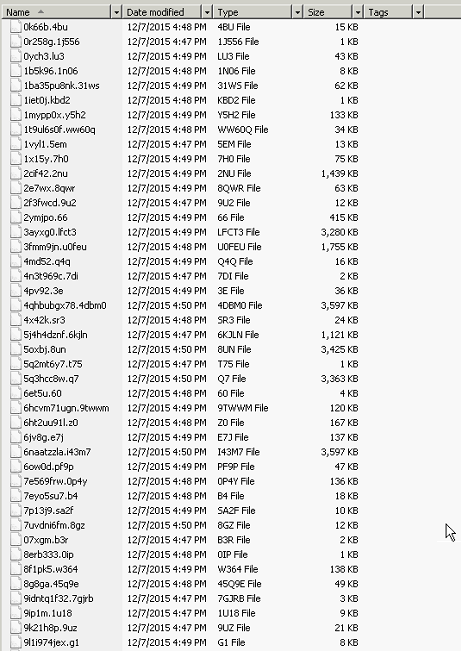
And the SqlScript directory within the Share directory had files with alphanumeric names all created within minutes of each other:
Resolution
If you have been infected on one machine your entire network is at risk. It would be a good idea to disconnect this machine from the network until the situation is dealt with. Otherwise you risk spreading the infection, particularly if you have employees with laptops that connect and disconnect from your network.
How do I get MIP up and Running after I have been infected?
Most customers who have been affected by this handle it in one of three ways
1)If they have good backups of the server machine they simply restore to a point prior to infection.
2)Install the software on a new server and copy the important files over
3)Back the important files up, reformat the existing server and install the software and restore the files.
What are the important files?
The critical files are the same ones you would back up as if you were following the instructions for moving servers (KB 876). They are:
-
Financial Databases- If you have a regular backup system in place you can use the backups its creates. If not you can log into SQL Studio Manager and back your databases up through that application (Right click on the database>Tasks>Backup). You will want to backup the regular databases as well as the database called NPSSQLSYS. The NPSSQLSYS contains the users, passwords and permissions.
-
Custom Formats – If you have custom check formats you will want to back those up as well. KB#5886 discusses how to find and move the custom formats. NOTE: It is possible that the cryptolocker may have encrypted your custom formats. If that is the case you will not be able to recover them unless you have a backup.
-
Attachments – If you use attachments you may need to move your attachments. KB#7206 Discusses how to do this. NOTE: It is possible that the Cryptolocker may have encrypted your attachments. If that is the case you will not be able to recover them unless you have a backup.
Other Applications – Some customers have 3rd party data applications that access MIP (timesheets, Crystal reports, Microix or other reporting tools). You would want to consult with someone familiar with those integrations to see what if anything would be required for those.
After the important files have been saved to a secure location (and scanned to make sure they are not infected) you will need to install the MIP software.
If you are installing on a new or reformatted server, you will need to install SQL server first before installing the application and then restoring the database. Consult the installation guide of the version you were on for any instructions or tips.
After you have reinstalled the MIP software you can restore your databases through the administration module (even if they were made through Studio Manager) and follow the KB for restoring your custom forms and attachments if needed.
Additional Information
Is it possible for me to just “clean” the infected machine and get MIP up and running?
It is possible; however customers who have used that option have reported being reinfected at a later date. They were not sure if it was a new infection or because the old infection was never completely cleaned.
If you want to go this route, you would need to completely uninstall the software (which may generate errors due to missing files) for both the workstation and the server. You would need to salvage your custom formats/attachments from the MIP SHARE folder. Then delete the MIP Share folder. When this is done you would reinstall the server and then workstation portions of the software. This is based on the theory that Crytolocker only affects items in a share folder which is what support has seen as of late 2014. Newer or more aggressive versions of the virus may go beyond share folders which would require additional troubleshooting which is beyond the scope of MIP Customer support.
Can I just pay the Ransom and get my files back?
It’s possible; some customers have reported paying the ransom and getting their data back. The ransom may be less money than you’d lose in time and productivity. But you’re sending an untracable payment to a criminal organization. There are no guarantees they will follow through and release the data. By paying the ransom you’re making this type of criminal behavior more profitable and encouraging it. If you do pay the ransom and get your data back, you would probably want to change/reformat servers unless you are very confident in your virus removal software.
How can I prevent this from happening again?
You can do some research about how Cryptolocker is spread and what you can do to prevent it.
A good article to start with is this: http://www.pcworld.com/article/2084002/how-to-rescue-your-pc-from-ransomware.html
Given that people have to use computers to get work done and new forms of malware are always coming out, a good backup strategy is crucial to have in order to save time, effort and data when all measures of prevention fail.
Article Type
Product Info
Product Line
MIP Fund Accounting
Fundraising 50
Product Module/Feature
Technical
Ranking
